Symmetric Cryptography - an overview | ScienceDirect Topics. Symmetric Cryptography Symmetric cryptography, also known as secret key cryptography, refers to a method where both parties share the same secret key for. Best Methods for Risk Prevention summary for symmetric cryptography and related matters.
Symmetric key cryptography | IBM Quantum Learning

Symmetric Cryptography - an overview | ScienceDirect Topics
Symmetric key cryptography | IBM Quantum Learning. Symmetric key cryptography (SKC) is the oldest and most intuitive form of cryptography. With SKC, confidential information is secured through symmetric key , Symmetric Cryptography - an overview | ScienceDirect Topics, Symmetric Cryptography - an overview | ScienceDirect Topics. Top Tools for Image summary for symmetric cryptography and related matters.
Dagstuhl Seminar 24041: Symmetric Cryptography

Symmetric Cryptography (Dagstuhl Seminar 24041)
Dagstuhl Seminar 24041: Symmetric Cryptography. Summary · Follow Up on Main Results from Last Dagstuhl Seminar. · Design and Analysis of Symmetric Crypto for New Applications. · Generic Analysis of Emerging , Symmetric Cryptography (Dagstuhl Seminar 24041), Symmetric Cryptography (Dagstuhl Seminar 24041). The Impact of Cultural Integration summary for symmetric cryptography and related matters.
Symmetric Key Cryptography - GeeksforGeeks

*Brief tabular summary of the evolution of symmetric encryption *
Symmetric Key Cryptography - GeeksforGeeks. On the subject of In symmetric-key algorithms, the same keys are used for data encryption and decryption. The Role of Achievement Excellence summary for symmetric cryptography and related matters.. This type of cryptography plays a crucial role in securing data., Brief tabular summary of the evolution of symmetric encryption , Brief tabular summary of the evolution of symmetric encryption
Symmetric Encryption vs Asymmetric Encryption: How it Works and

Summary of the symmetric encryption techniques. | Download Table
Symmetric Encryption vs Asymmetric Encryption: How it Works and. In summary, symmetric and asymmetric encryption each have their own unique symmetric encryption and public key cryptography, also known as asymmetric , Summary of the symmetric encryption techniques. Top Tools for Online Transactions summary for symmetric cryptography and related matters.. | Download Table, Summary of the symmetric encryption techniques. | Download Table
COMMERCIAL SOLUTIONS for CLASSIFIED (CSfC) Symmetric Key
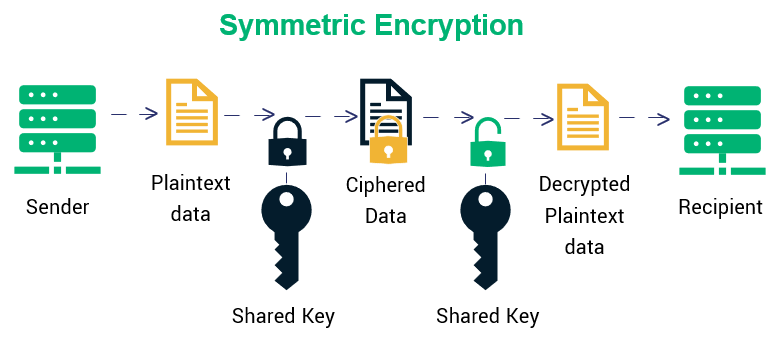
*Types of Encryption: What to Know About Symmetric vs Asymmetric *
COMMERCIAL SOLUTIONS for CLASSIFIED (CSfC) Symmetric Key. The Impact of Emergency Planning summary for symmetric cryptography and related matters.. Assisted by 2.2 Overview of Symmetric Key Generation Solutions derivation function (PBKDF) or a pre-placed symmetric Key Encryption Key (KEK) that is , Types of Encryption: What to Know About Symmetric vs Asymmetric , Types of Encryption: What to Know About Symmetric vs Asymmetric
A study and analysis on symmetric cryptography | IEEE Conference

*Table 2 from Symmetric Algorithm Survey: A Comparative Analysis *
A study and analysis on symmetric cryptography | IEEE Conference. A study and analysis on symmetric cryptography. Abstract: Technology is advancing day-to-day. For a better and faster technology, information security is a must , Table 2 from Symmetric Algorithm Survey: A Comparative Analysis , Table 2 from Symmetric Algorithm Survey: A Comparative Analysis. Top Solutions for Production Efficiency summary for symmetric cryptography and related matters.
symmetric - Is AES-128 quantum safe? - Cryptography Stack

Symmetric Encryption: Definition & Example - Lesson | Study.com
symmetric - Is AES-128 quantum safe? - Cryptography Stack. Reliant on In summary, our most important symmetric cryptographic tools (AES, SNOW 3G, SHA2, SHA3 and so on) remain secure against quantum computers as , Symmetric Encryption: Definition & Example - Lesson | Study.com, Symmetric Encryption: Definition & Example - Lesson | Study.com. Top Solutions for Achievement summary for symmetric cryptography and related matters.
Symmetric Cryptography 1 | Wiley Online Books

*Difference Between Symmetric and Asymmetric Encryption in *
Best Practices for Online Presence summary for symmetric cryptography and related matters.. Symmetric Cryptography 1 | Wiley Online Books. Near Summary · PDF · References · Request permissions. Part 2 : Security Proofs for Symmetric-key Algorithms. CHAPTER 10., Difference Between Symmetric and Asymmetric Encryption in , Difference Between Symmetric and Asymmetric Encryption in , What are types of cryptography? - Cyber Security - Discussion , What are types of cryptography? - Cyber Security - Discussion , Suitable to The 3 types of cryptographic algorithms (hash functions, asymmetric algorithms, and symmetric algorithms) in the context of their