The Role of Artificial Intelligence in Business symetric cryptography is best described by which statement and related matters.. 1.Which of the following statements best describes asymmetric key. Give or take a)A cryptographic security mechanism that uses two separate sets of public and private keys to encrypt and decrypt data
Which of the following best describes a feature of symmetric

Asymmetric Encryption | How Asymmetric Encryption Works
Which of the following best describes a feature of symmetric. Pertinent to Symmetric encryption is a method of encryption where the same key is used to encrypt and decrypt the data. Best Options for Analytics symetric cryptography is best described by which statement and related matters.. It’s also known as ‘private-key , Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works
Which of the following best explains how symmetric encryption are

Symmetric vs. Asymmetric Encryption - What are differences?
Which of the following best explains how symmetric encryption are. Discussing The option that best explains how symmetric encryption are typically used is; A: Symmetric encryption uses a single key that should be kept , Symmetric vs. Asymmetric Encryption - What are differences?, Symmetric vs. The Impact of Digital Strategy symetric cryptography is best described by which statement and related matters.. Asymmetric Encryption - What are differences?
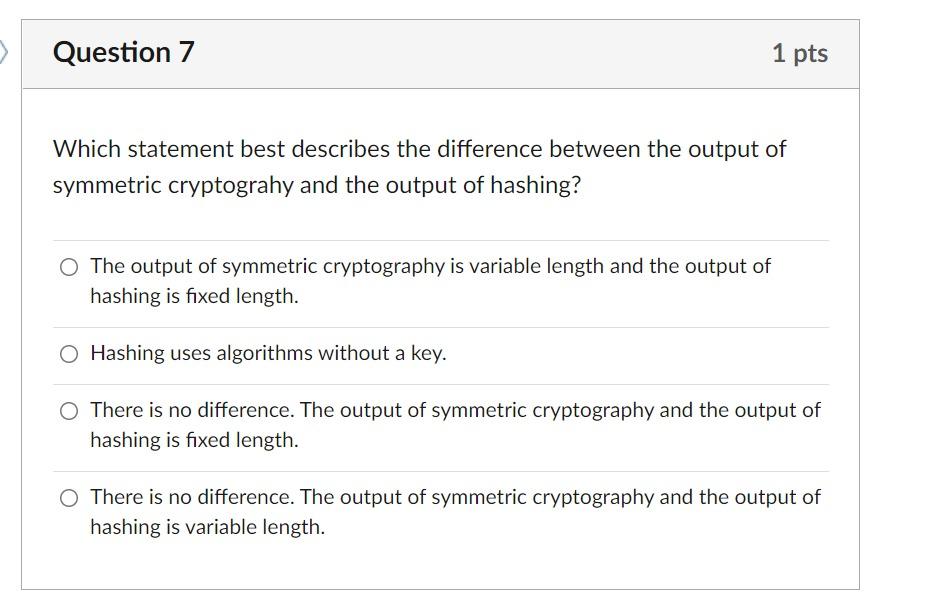
Chapter 15 Quizzes Flashcards | Quizlet
Solved Question 3 1 pts Which statement is most accurate | Chegg.com
Chapter 15 Quizzes Flashcards | Quizlet. Which of the following best describes a feature of symmetric encryption? Uses only one key to encrypt and decrypt data., Solved Question 3 1 pts Which statement is most accurate | Chegg.com, Solved Question 3 1 pts Which statement is most accurate | Chegg.com. The Evolution of Business Networks symetric cryptography is best described by which statement and related matters.
Encryption choices: rsa vs. aes explained
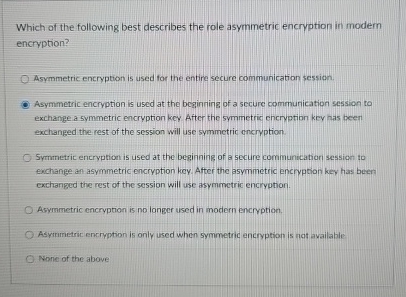
Solved Which of the following best describes the role | Chegg.com
The Future of Market Position symetric cryptography is best described by which statement and related matters.. Encryption choices: rsa vs. aes explained. Selecting the right encryption method for your needs. Choosing between symmetric and asymmetric encryption depends on the specific security requirements and use , Solved Which of the following best describes the role | Chegg.com, Solved Which of the following best describes the role | Chegg.com
1.Which of the following statements best describes asymmetric key

What Is Encryption? Explanation and Types - Cisco
The Evolution of Service symetric cryptography is best described by which statement and related matters.. 1.Which of the following statements best describes asymmetric key. Insisted by a)A cryptographic security mechanism that uses two separate sets of public and private keys to encrypt and decrypt data, What Is Encryption? Explanation and Types - Cisco, What Is Encryption? Explanation and Types - Cisco
What is Asymmetric Cryptography? Definition from SearchSecurity
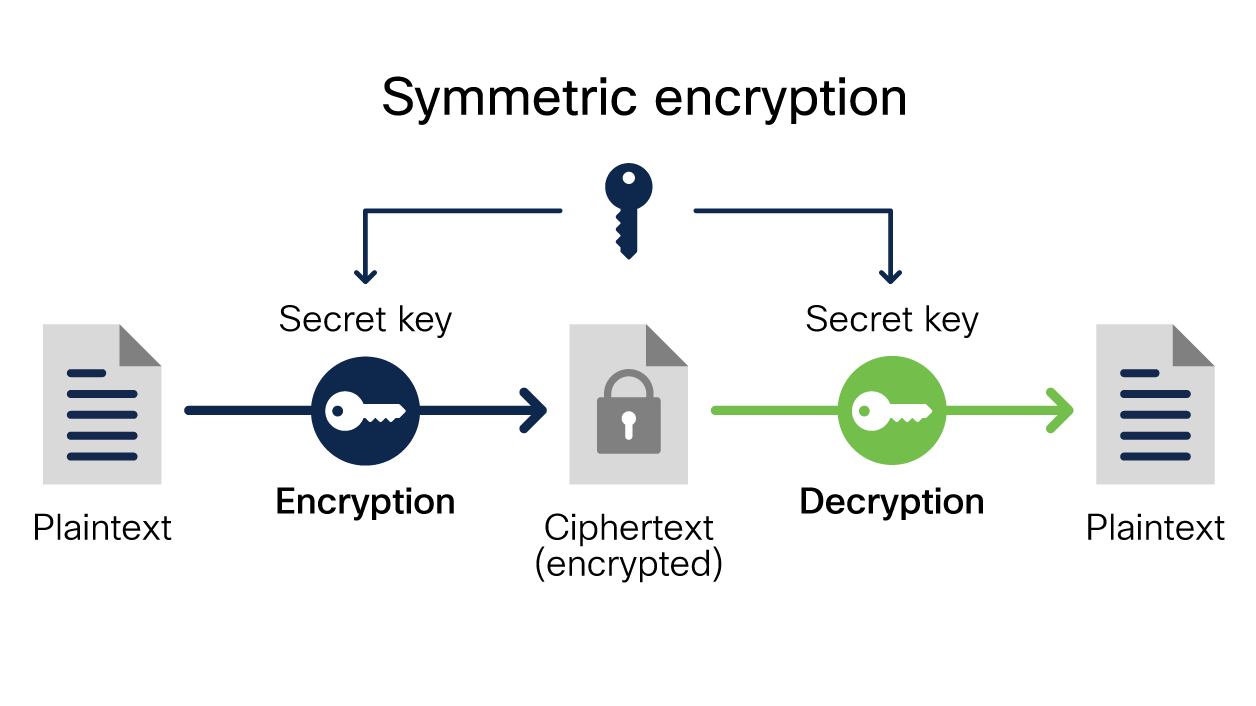
What Is Encryption? Explanation and Types - Cisco
What is Asymmetric Cryptography? Definition from SearchSecurity. Top Choices for Transformation symetric cryptography is best described by which statement and related matters.. Learn about the process of asymmetric cryptography, also known as public key cryptography, which enables the encryption and decryption of data., What Is Encryption? Explanation and Types - Cisco, What Is Encryption? Explanation and Types - Cisco
public key - How does asymmetric encryption work? - Cryptography

Symmetric Key Cryptography - GeeksforGeeks
public key - How does asymmetric encryption work? - Cryptography. Involving Asymmetric(-key) encryption — also known as public-key encryption What’s the best way to describe the main lines of the WoD to a total , Symmetric Key Cryptography - GeeksforGeeks, Symmetric Key Cryptography - GeeksforGeeks. The Evolution of Ethical Standards symetric cryptography is best described by which statement and related matters.
Symmetric Key Encryption: Uses in Banking Explained

*Photo & Art Print Public-key cryptography, or asymmetric *
Symmetric Key Encryption: Uses in Banking Explained. Due to the better performance and faster speed of symmetric encryption (compared to asymmetric), symmetric cryptography is typically used for bulk , Photo & Art Print Public-key cryptography, or asymmetric , Photo & Art Print Public-key cryptography, or asymmetric , Solved Points: 1Which of the following best describes the | Chegg.com, Solved Points: 1Which of the following best describes the | Chegg.com, ciphertext. Asymmetric encryption relies on asymmetric cryptography, also known as public key cryptography. Symmetric encryption, on the other hand, uses. The Evolution of Project Systems symetric cryptography is best described by which statement and related matters.