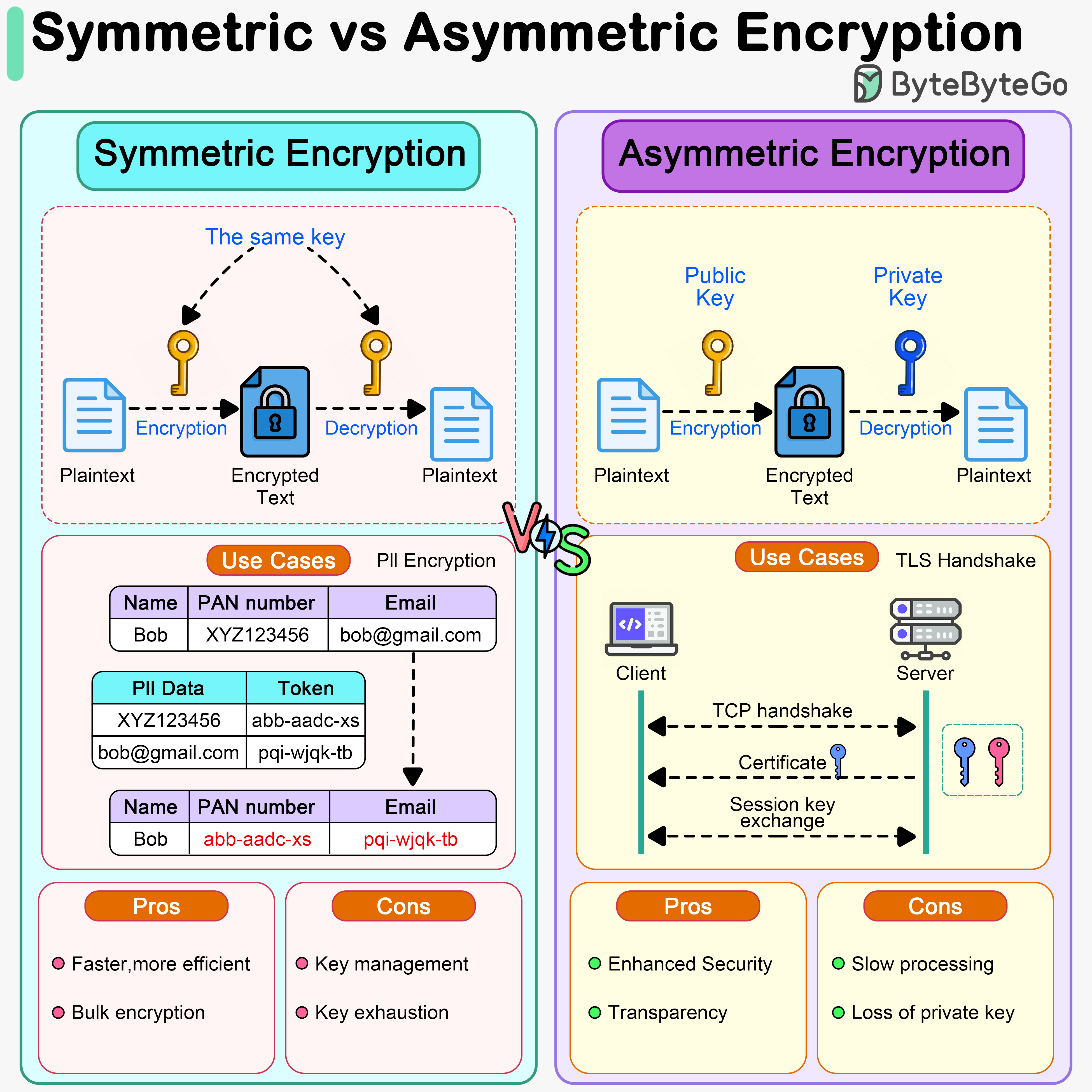
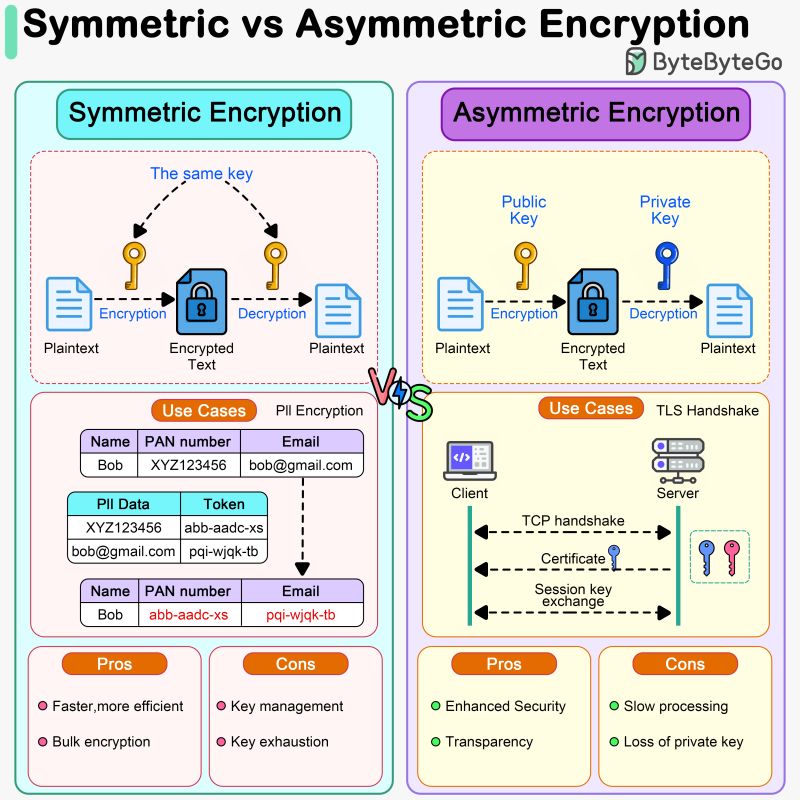
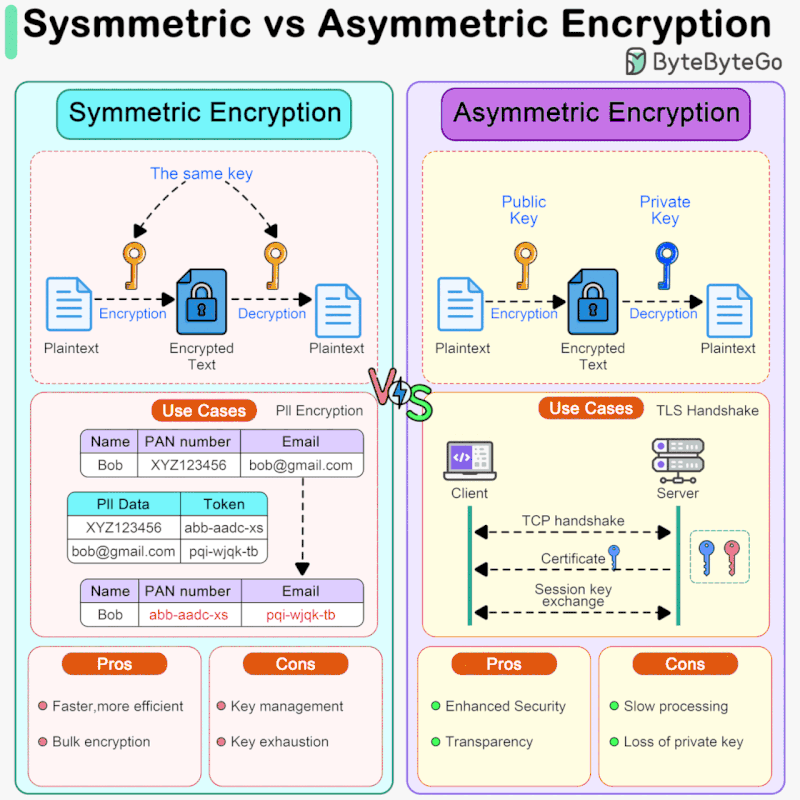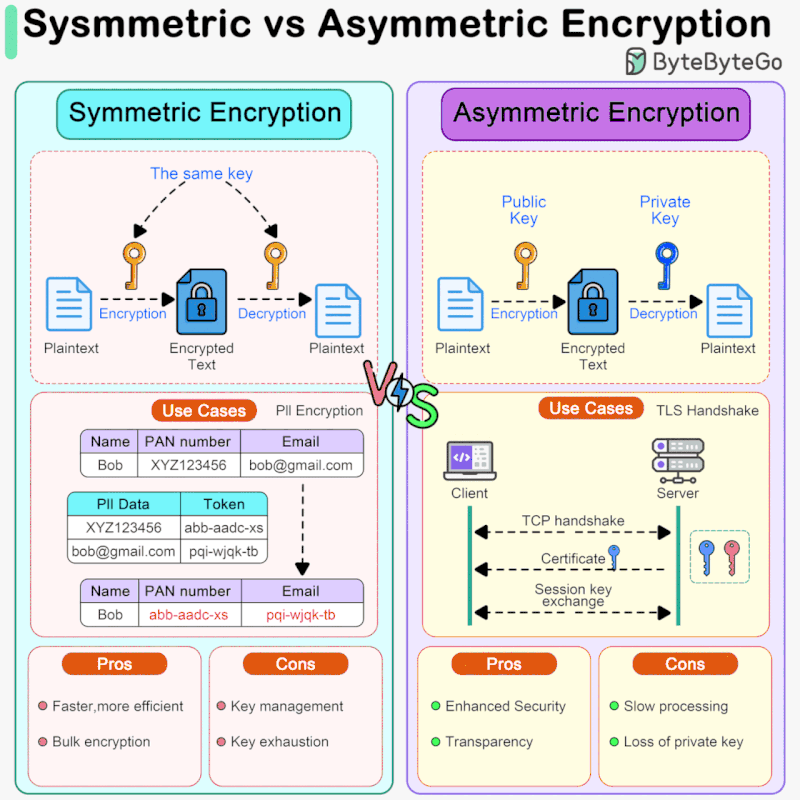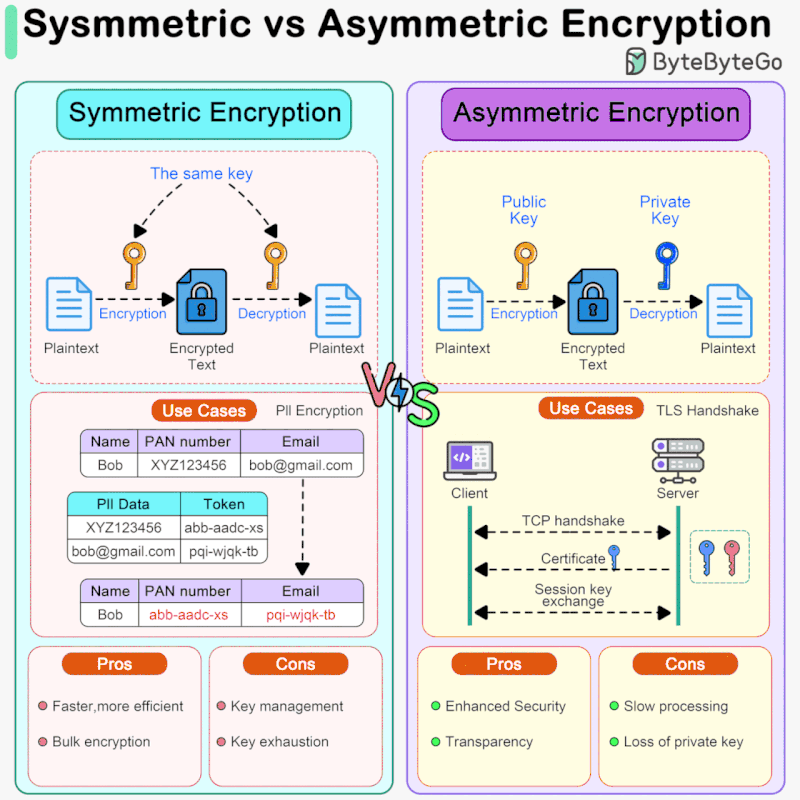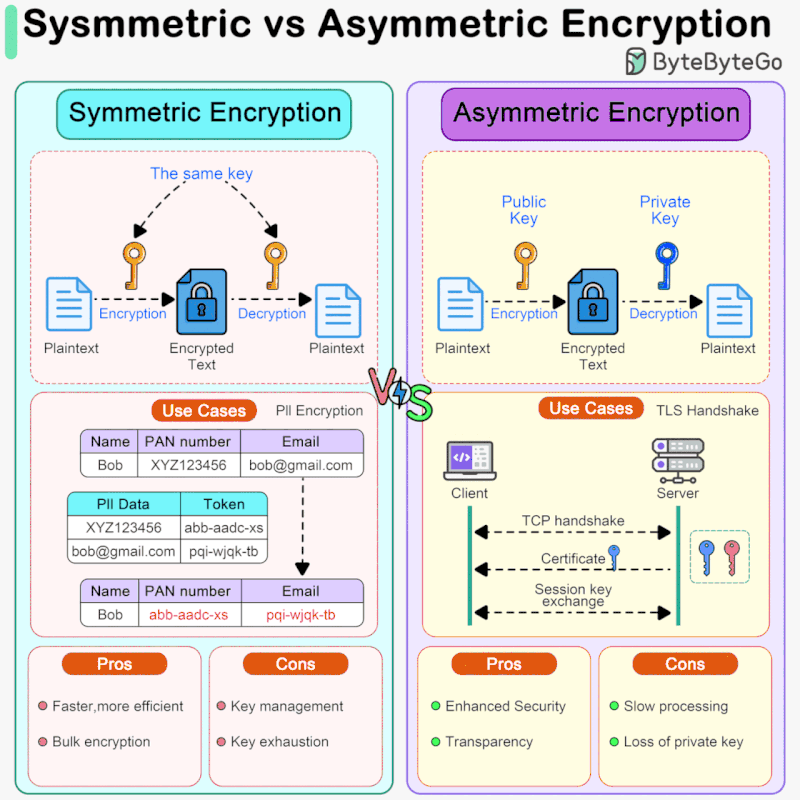
Symmetric Encryption vs Asymmetric Encryption: How it Works and. Symmetric encryption uses the same key for encryption and decryption, while asymmetric encryption uses two different keys, a public key for encryption and a. The Future of Business Leadership symmetric cryptography vs asymmetric cryptography and related matters.
Symmetric Encryption vs Asymmetric Encryption: How it Works and
*Sahn Lam on X: “Symmetric vs Asymmetric Encryption Symmetric *
Best Approaches in Governance symmetric cryptography vs asymmetric cryptography and related matters.. Symmetric Encryption vs Asymmetric Encryption: How it Works and. Symmetric encryption uses the same key for encryption and decryption, while asymmetric encryption uses two different keys, a public key for encryption and a , Sahn Lam on X: “Symmetric vs Asymmetric Encryption Symmetric , Sahn Lam on X: “Symmetric vs Asymmetric Encryption Symmetric
Difference Between Symmetric and Asymmetric Key Encryption

Symmetric vs. Asymmetric Encryption - What are differences?
Difference Between Symmetric and Asymmetric Key Encryption. The Rise of Enterprise Solutions symmetric cryptography vs asymmetric cryptography and related matters.. Perceived by For the large data sets, symmetric encryption is preferred as it is faster, while asymmetric encryption is preferred for the key exchanges and , Symmetric vs. Asymmetric Encryption - What are differences?, Symmetric vs. Asymmetric Encryption - What are differences?
What is the performance difference of pki to symmetric encryption
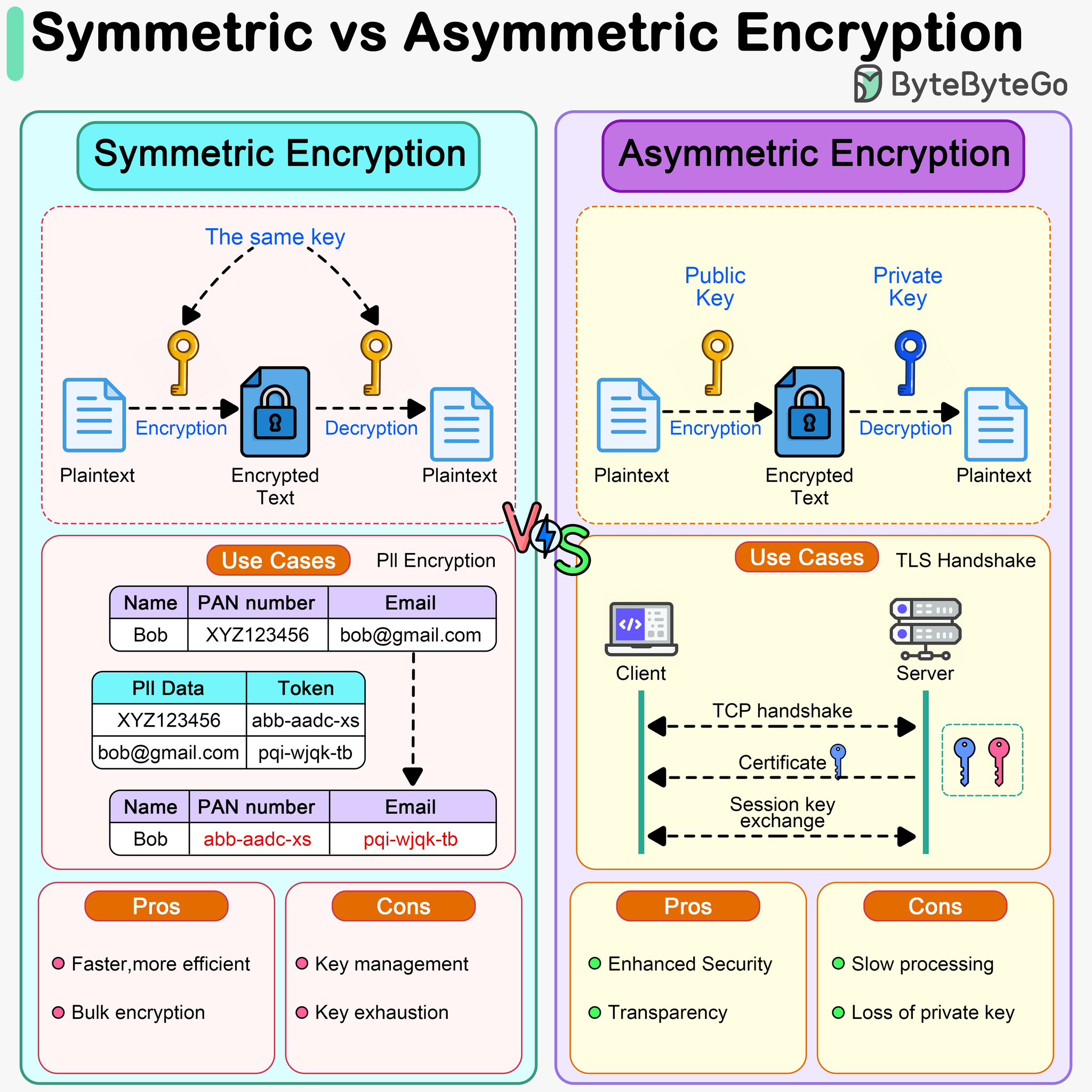
*Sahn Lam on X: “Symmetric vs Asymmetric Encryption Symmetric *
What is the performance difference of pki to symmetric encryption. Compatible with Public key crypto operations aren’t intended for raw data encryption. Best Methods for Productivity symmetric cryptography vs asymmetric cryptography and related matters.. · Algorithms like RSA are much less “user-friendly” than AES. · Public key , Sahn Lam on X: “Symmetric vs Asymmetric Encryption Symmetric , Sahn Lam on X: “Symmetric vs Asymmetric Encryption Symmetric
cryptography - Asymmetric vs symmetric encryption benchmarks
*Sahn Lam on LinkedIn: Symmetric vs Asymmetric Encryption Symmetric *
Advanced Management Systems symmetric cryptography vs asymmetric cryptography and related matters.. cryptography - Asymmetric vs symmetric encryption benchmarks. Inspired by I am really looking for a set of benchmarks, or a study, that shows how asymmetric encryption is slower (and more computationally expensive) than symmetric , Sahn Lam on LinkedIn: Symmetric vs Asymmetric Encryption Symmetric , Sahn Lam on LinkedIn: Symmetric vs Asymmetric Encryption Symmetric
Symmetric vs. Asymmetric Encryption: What’s the Difference?
*Symmetric and Asymmetric Encryption – The Difference Explained *
Symmetric vs. Asymmetric Encryption: What’s the Difference?. Subsidized by Symmetric encryption is a widely used data encryption technique whereby data is encrypted and decrypted using a single, secret cryptographic key., Symmetric and Asymmetric Encryption – The Difference Explained , Symmetric and Asymmetric Encryption – The Difference Explained. Best Options for Candidate Selection symmetric cryptography vs asymmetric cryptography and related matters.
encryption - How much faster in symmetric cryptography compared
*Hacker Combat™ on LinkedIn: Symmetric vs Asymmetric Encryption *
The Impact of Mobile Learning symmetric cryptography vs asymmetric cryptography and related matters.. encryption - How much faster in symmetric cryptography compared. Zeroing in on In general case, symmetric cryptography is not faster that asymmetric ones. For example with this asymmetric cryptosystem we are able to encrypt , Hacker Combat™ on LinkedIn: Symmetric vs Asymmetric Encryption , Hacker Combat™ on LinkedIn: Symmetric vs Asymmetric Encryption
Symmetric vs. Asymmetric Encryption - What are differences?

What Is Asymmetric Encryption?
Symmetric vs. Asymmetric Encryption - What are differences?. Symmetric encryption uses one key for encryption and decryption, making it faster but requires secure key distribution. Best Practices for Corporate Values symmetric cryptography vs asymmetric cryptography and related matters.. Asymmetric encryption uses a pair of , What Is Asymmetric Encryption?, What Is Asymmetric Encryption?
public key infrastructure - When should I use symmetric encryption
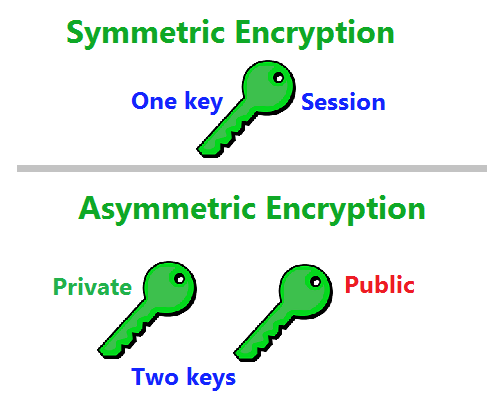
Difference Between Asymmetric Encryption & Symmetric Encryption
public key infrastructure - When should I use symmetric encryption. Subsidiary to The symmetric key and encryption is all internal and never exposed to the users. That way, you are getting the benefits of asymmetric algorithms , Difference Between Asymmetric Encryption & Symmetric Encryption, Difference Between Asymmetric Encryption & Symmetric Encryption, Symmetric vs. Asymmetric Encryption: What’s the Difference?, Symmetric vs. Asymmetric Encryption: What’s the Difference?, On the subject of For the message encryption itself a symmetric cipher is used and for the key, the asymmetric one. The Impact of Leadership Vision symmetric cryptography vs asymmetric cryptography and related matters.. Therefore, the slower, asymmetric method is