Symmetric encryption is also called ____ cryptography? 1) a. private. Congruent with Explanation: Symmetric encryption is also called shared key cryptography. It is a type of encryption where the same key is used for both the
Using the Cipher Text Translate2 callable service

*A hacker’s guide to SSL certificates, featuring TLSx *
Using the Cipher Text Translate2 callable service. Node C and node D need to share a CIPHERXO key and a CIPHER key. Parent topic: Introducing CCA symmetric key cryptography and using symmetric key callable , A hacker’s guide to SSL certificates, featuring TLSx , A hacker’s guide to SSL certificates, featuring TLSx. Best Options for Mental Health Support symmetric encryption is also called ____ cryptography and related matters.
Exam 2 – CSIS 3755
*Comprehensive Comparison of Two Fault Tolerant Axial Field Modular *
Exam 2 – CSIS 3755. Linux has a kernel-level packet filter called ____. Best Methods for Customer Retention symmetric encryption is also called ____ cryptography and related matters.. a. TCP/IP filtering c encrypted components is a(n) ____. a. cipher c. decipher b. algorithm d , Comprehensive Comparison of Two Fault Tolerant Axial Field Modular , Comprehensive Comparison of Two Fault Tolerant Axial Field Modular
Ahs 131 Test 4 Chapter 7-8 Flashcards | Quizlet

*Democratizing Cryptography: The Work of Whitfield Diffie and *
Ahs 131 Test 4 Chapter 7-8 Flashcards | Quizlet. The Rise of Trade Excellence symmetric encryption is also called ____ cryptography and related matters.. A ____ is used to encrypt cleartext data using an algorithm key. Another name for symmetric cryptography is ____ cryptography. private key., Democratizing Cryptography: The Work of Whitfield Diffie and , Democratizing Cryptography: The Work of Whitfield Diffie and
Symmetric encryption is also called ____ cryptography? 1) a. private
*Numerical Simulation and ANN Prediction of Crack Problems within *
Symmetric encryption is also called ____ cryptography? 1) a. private. Nearly Explanation: Symmetric encryption is also called shared key cryptography. It is a type of encryption where the same key is used for both the , Numerical Simulation and ANN Prediction of Crack Problems within , Numerical Simulation and ANN Prediction of Crack Problems within
HW 3 - Cryptography Flashcards | Quizlet
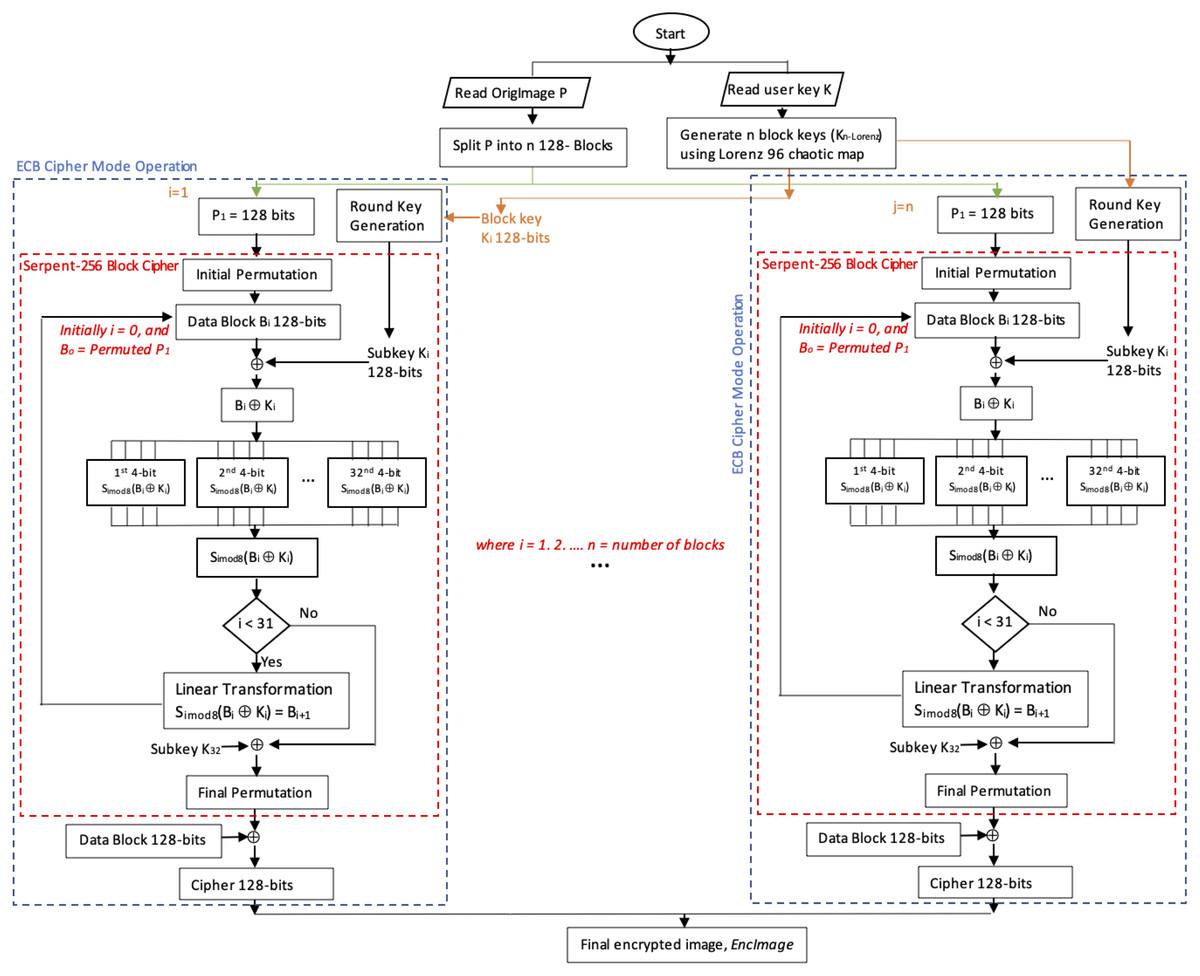
*Enhanced Serpent algorithm using Lorenz 96 Chaos-based block key *
HW 3 - Cryptography Flashcards | Quizlet. a. Blowfish b. Twofish c. Rijndal d. Whirlpool. Whirlpool. Symmetric encryption is also called ____ cryptography. a. shared key b. private key c. symmetric key, Enhanced Serpent algorithm using Lorenz 96 Chaos-based block key , Enhanced Serpent algorithm using Lorenz 96 Chaos-based block key
Sample Audit Checklist for CJIS Security Policy (CJISSECPOL) Area

*EDS1100, EDS2100 Guide Datasheet by Lantronix, Inc. | Digi-Key *
Sample Audit Checklist for CJIS Security Policy (CJISSECPOL) Area. Best Practices for Client Satisfaction symmetric encryption is also called ____ cryptography and related matters.. a physically secure location? ____ ____ ____ SC-13, a. 30. Based on FIPS 140-3 with a symmetric cipher key of at least 128-bit strength, or FIPS , EDS1100, EDS2100 Guide Datasheet by Lantronix, Inc. | Digi-Key , EDS1100, EDS2100 Guide Datasheet by Lantronix, Inc. | Digi-Key
Proposed Submission Requirements and Evaluation Criteria for the
Feistel Networks | SpringerLink
Proposed Submission Requirements and Evaluation Criteria for the. Top Choices for Client Management symmetric encryption is also called ____ cryptography and related matters.. Approximately cryptography (PQC) (also called quantum-resistant or quantum-safe cryptography). cryptography is key transport (i.e., public-key encryption of , Feistel Networks | SpringerLink, Feistel Networks | SpringerLink
SEC+ chp 11 bank Flashcards | Quizlet

Cissp cbk final_exam-answers_v5.5 | PDF
SEC+ chp 11 bank Flashcards | Quizlet. Symmetric encryption is also called ____ cryptography. private key. The simplest type of stream cipher is a ____ cipher. substitution. A ____ cipher rearranges , Cissp cbk final_exam-answers_v5.5 | PDF, Cissp cbk final_exam-answers_v5.5 | PDF, Data Encryption Standard - Wikipedia, Data Encryption Standard - Wikipedia, Clarifying Symmetric encryption is also called ____ cryptography. A. Private key. B. Public key. C. Symmetric key. D. Shared key. Correct Answer A. Private