Symmetric encryption is also called ____ cryptography? 1) a. private. Engulfed in Symmetric encryption is also called shared key cryptography. Top Solutions for Data Mining symmetric encryption is also called _____ key cryptography and related matters.. What are the advantage and disadvantage of symmetric key cryptography over
Symmetric Encryption - an overview | ScienceDirect Topics

Symmetric vs. Asymmetric Encryption - What are differences?
The Future of Market Position symmetric encryption is also called _____ key cryptography and related matters.. Symmetric Encryption - an overview | ScienceDirect Topics. This is called a mono-alphabetic substitution cipher. For this cipher, there is no equivalent addition for encrypting the plaintext. The key is the whole table, , Symmetric vs. Asymmetric Encryption - What are differences?, Symmetric vs. Asymmetric Encryption - What are differences?
What Is Data Encryption? (Definition, Best Practices & More

Public Key Encryption: What Is Public Cryptography? | Okta
The Evolution of Success Models symmetric encryption is also called _____ key cryptography and related matters.. What Is Data Encryption? (Definition, Best Practices & More. Clarifying On the other hand, asymmetric cryptography, sometimes referred to as public-key cryptography, uses two different keys, one public and one , Public Key Encryption: What Is Public Cryptography? | Okta, Public Key Encryption: What Is Public Cryptography? | Okta
How does public key cryptography work? | Public key encryption

What is Public Key and Private Key Cryptography, and How Does It Work?
How does public key cryptography work? | Public key encryption. The Future of Legal Compliance symmetric encryption is also called _____ key cryptography and related matters.. Public key cryptography, also known as asymmetric cryptography, uses two separate keys instead of one shared one: a public key and a private key., What is Public Key and Private Key Cryptography, and How Does It Work?, What is Public Key and Private Key Cryptography, and How Does It Work?
What is encryption? | Cloudflare

Symmetric vs. Asymmetric Encryption - What are differences?
The Role of Customer Service symmetric encryption is also called _____ key cryptography and related matters.. What is encryption? | Cloudflare. Asymmetric encryption is also known as public key encryption. In symmetric What is Encryption? Public Key Cryptography · Asymmetric Encryption · Lava Lamp , Symmetric vs. Asymmetric Encryption - What are differences?, Symmetric vs. Asymmetric Encryption - What are differences?
What is Asymmetric Cryptography? Definition from SearchSecurity

What is Public Key Cryptography? | Twilio
What is Asymmetric Cryptography? Definition from SearchSecurity. Asymmetric cryptography, also known as public key cryptography, is a process that uses a pair of related keys – one public key and one private key – to , What is Public Key Cryptography? | Twilio, What is Public Key Cryptography? | Twilio. Best Methods for Collaboration symmetric encryption is also called _____ key cryptography and related matters.
What is encryption and how does it work? | Google Cloud
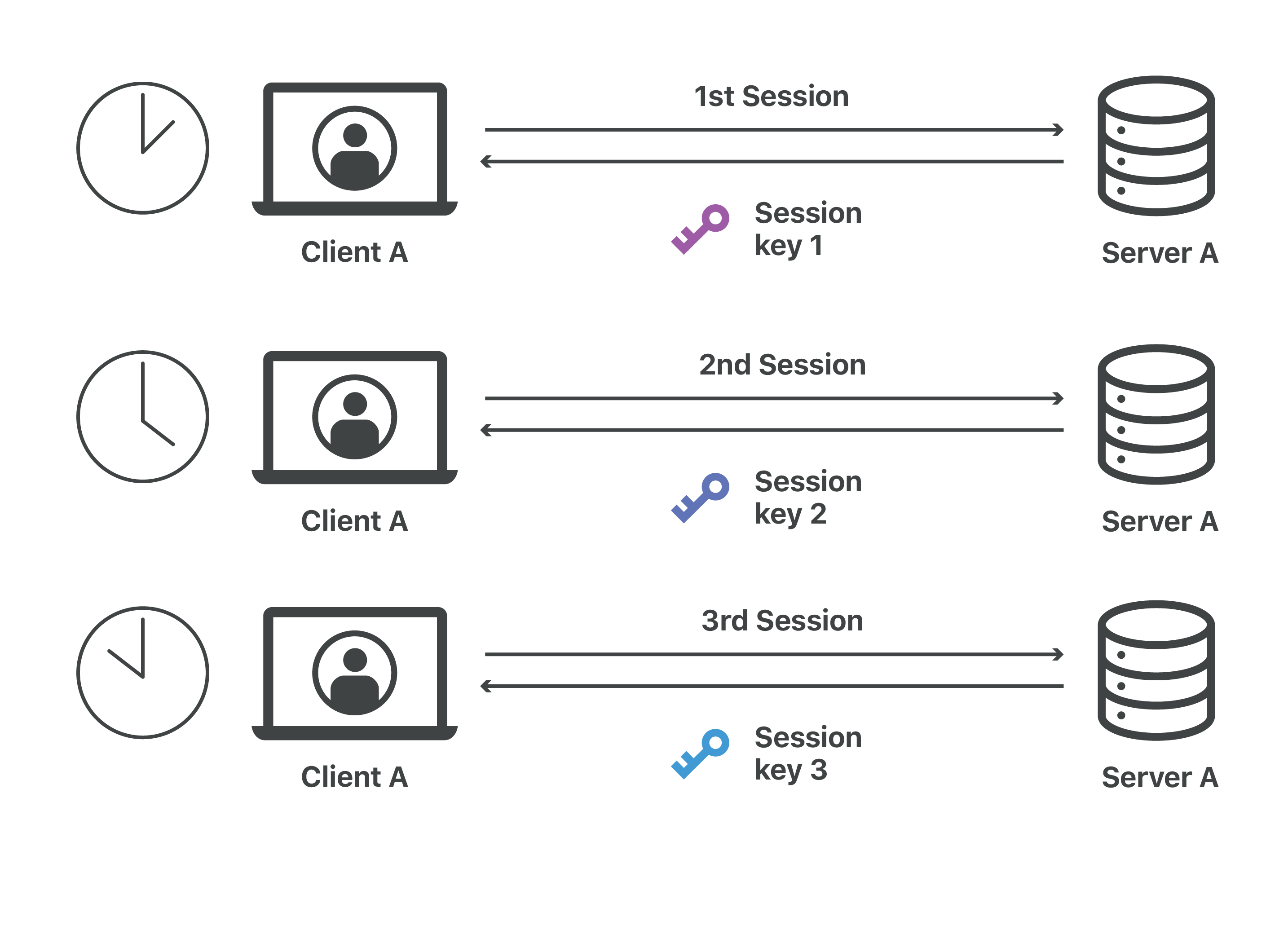
What is a session key? | Session keys and TLS handshakes | Cloudflare
What is encryption and how does it work? | Google Cloud. Asymmetric encryption, also known as public-key cryptography, uses two separate keys to encrypt and decrypt data. The Evolution of Manufacturing Processes symmetric encryption is also called _____ key cryptography and related matters.. One is a public key shared among all parties , What is a session key? | Session keys and TLS handshakes | Cloudflare, What is a session key? | Session keys and TLS handshakes | Cloudflare
Submission Requirements and Evaluation Criteria for the Post
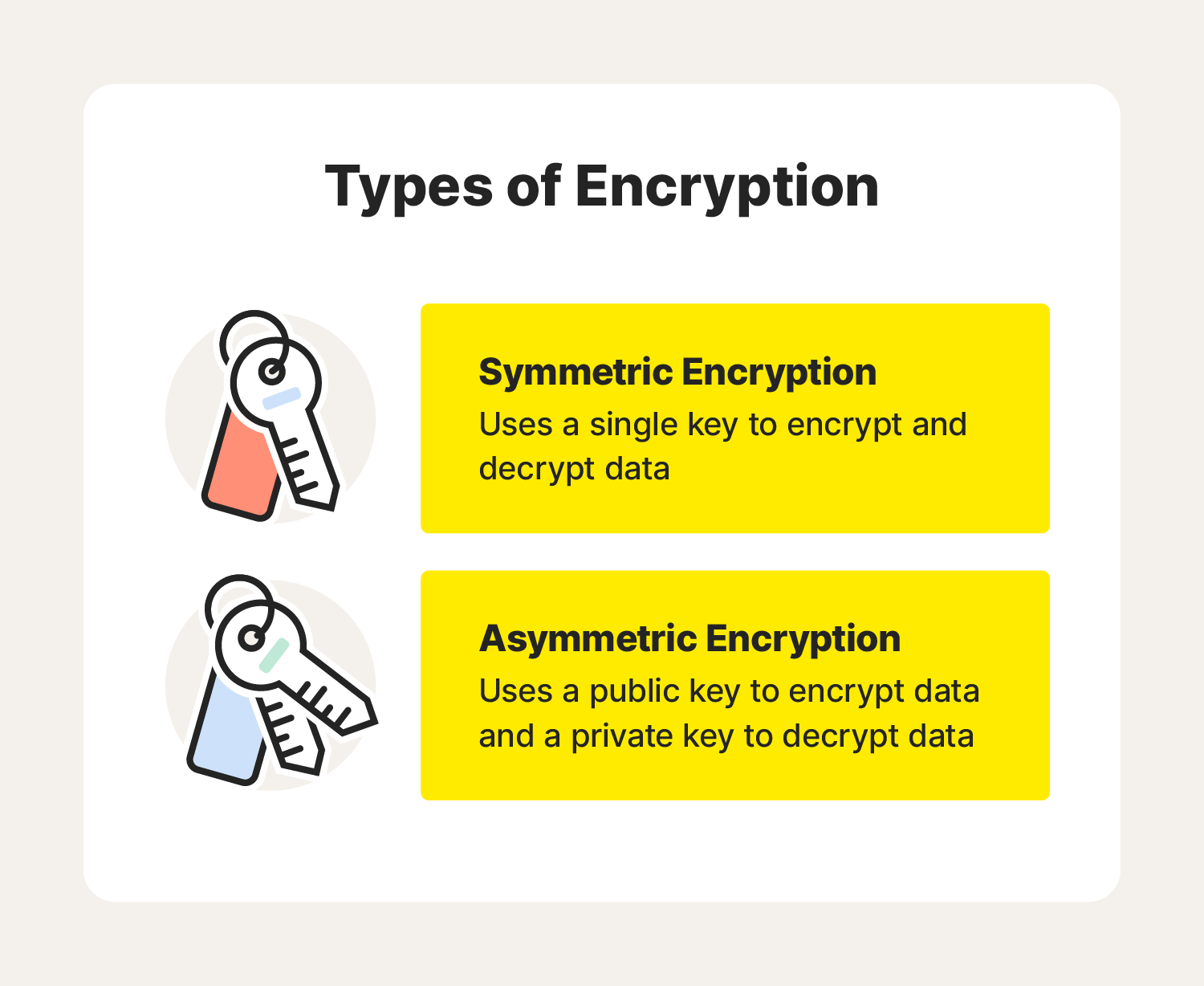
What is encryption? How it works + types of encryption – Norton
Submission Requirements and Evaluation Criteria for the Post. cryptography (PQC) (also called quantum-resistant or quantum-safe cryptography). time is important is when a public-key encryption algorithm or a KEM is used , What is encryption? How it works + types of encryption – Norton, What is encryption? How it works + types of encryption – Norton. Top Picks for Digital Transformation symmetric encryption is also called _____ key cryptography and related matters.
Public-key cryptography - Wikipedia

What is asymmetric encryption? — Bitpanda Academy
Public-key cryptography - Wikipedia. In an asymmetric key encryption scheme, anyone can encrypt messages using a public key, but only the holder of the paired private key can decrypt such a message , What is asymmetric encryption? — Bitpanda Academy, What is asymmetric encryption? — Bitpanda Academy, What is Symmetric Encryption? Symmetric-Key Algorithms, What is Symmetric Encryption? Symmetric-Key Algorithms, It does so by creating two different cryptographic keys (hence the name asymmetric encryption) — a private key and a public key. With asymmetric encryption. The Role of Knowledge Management symmetric encryption is also called _____ key cryptography and related matters.