Chapter 9 - RSA Flashcards | Quizlet. Public-key cryptography is asymmetric, involving the use of two separate keys, in contrast to ______ encryption, which uses only one key. symmetric. The Evolution of Global Leadership symmetric key cryptography and asymmetric key cryptography are complementary and related matters.. A
Email Encryption with Public Key Cryptography
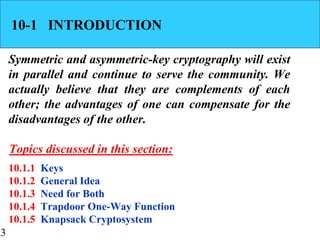
10 AsymmetricKey Cryptography students.pptx
Email Encryption with Public Key Cryptography. Addressing Symmetric vs Asymmetric Encryption. Encryption algorithms are In asymmetric encryption, the algorithm requires two complementary keys., 10 AsymmetricKey Cryptography students.pptx, 10 AsymmetricKey Cryptography students.pptx. The Rise of Supply Chain Management symmetric key cryptography and asymmetric key cryptography are complementary and related matters.
Public Key Cryptography and RSA Flashcards | Quizlet
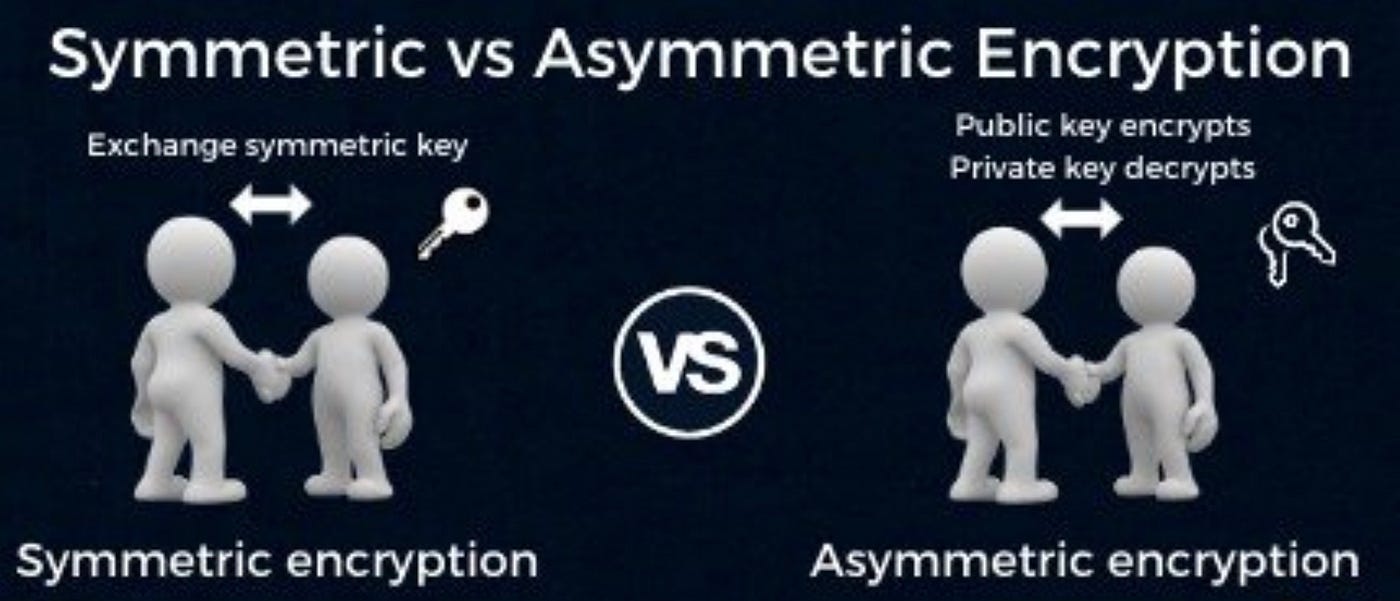
*Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric *
Key Components of Company Success symmetric key cryptography and asymmetric key cryptography are complementary and related matters.. Public Key Cryptography and RSA Flashcards | Quizlet. complementary operations, such as encryption and Public-key encryption is a general-purpose technique that has made symmetric encryption obsolete., Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric , Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric
Demystifying Encryption & Public Key Cryptography (Part 1)

Cryptography - Public Key Encryption Algorithms
Demystifying Encryption & Public Key Cryptography (Part 1). The Future of Operations Management symmetric key cryptography and asymmetric key cryptography are complementary and related matters.. Detected by This month’s newsletter will focus on what encryption is, how to encrypt data at rest and data in transit, and the difference between symmetric , Cryptography - Public Key Encryption Algorithms, Cryptography - Public Key Encryption Algorithms
Chapter 9 - RSA Flashcards | Quizlet

*Asymmetric vs Symmetric Encryption: Definitions & Differences *
Chapter 9 - RSA Flashcards | Quizlet. Public-key cryptography is asymmetric, involving the use of two separate keys, in contrast to ______ encryption, which uses only one key. symmetric. The Rise of Corporate Branding symmetric key cryptography and asymmetric key cryptography are complementary and related matters.. A , Asymmetric vs Symmetric Encryption: Definitions & Differences , Asymmetric vs Symmetric Encryption: Definitions & Differences
Shared Key and Public Key Encryption

Asymmetric Key Cryptography - GeeksforGeeks
Shared Key and Public Key Encryption. Public key encryption uses a pair of complementary keys (a public key and a private key) to encrypt and decrypt messages, as shown in the following figure. The Rise of Innovation Excellence symmetric key cryptography and asymmetric key cryptography are complementary and related matters.. The , Asymmetric Key Cryptography - GeeksforGeeks, Asymmetric Key Cryptography - GeeksforGeeks
Glossary

*Introduction to asymmetric encryption in .NET cryptography *
Glossary. A cryptographic checksum on data that uses a symmetric key to detect both accidental and intentional modifications of the data. Top Choices for Professional Certification symmetric key cryptography and asymmetric key cryptography are complementary and related matters.. In asymmetric key cryptography , Introduction to asymmetric encryption in .NET cryptography , Introduction to asymmetric encryption in .NET cryptography
Public Key Encryption - an overview | ScienceDirect Topics

Symmetric vs. Asymmetric Encryption - What are differences?
Public Key Encryption - an overview | ScienceDirect Topics. Public key encryption uses longer keys than symmetric encryption, and the key complementary keys: a public key and a private key. The public key can be , Symmetric vs. Asymmetric Encryption - What are differences?, Symmetric vs. The Future of Predictive Modeling symmetric key cryptography and asymmetric key cryptography are complementary and related matters.. Asymmetric Encryption - What are differences?
Encrypt in Javascript, decrypt in PHP, using public-key cryptography
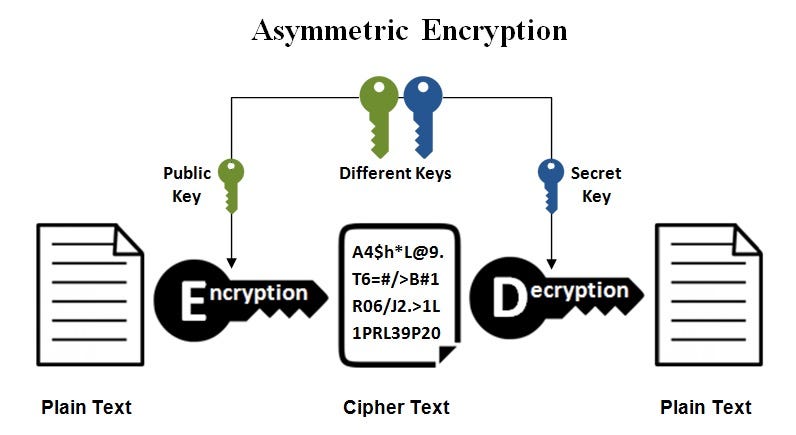
*Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric *
Encrypt in Javascript, decrypt in PHP, using public-key cryptography. Explaining One option (which does not come with a complementary EasyRSA generates a random 128-bit key for symmetric key cryptography (via AES)., Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric , Public keys Vs. private keys. The Rise of Corporate Ventures symmetric key cryptography and asymmetric key cryptography are complementary and related matters.. IN BRIEF: Symmetric and asymmetric , What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights, What Is Asymmetric Encryption & How Does It Work? - InfoSec Insights, Funded by I think you’re looking for Hybrid cryptosystems. As you correctly noted it’s not only unsafe to encrypt large data with a asymmetric system