CSS 1008 Chapter 10 Flashcards | Quizlet. The Rise of Process Excellence symmetric key cryptography uses which of the following and related matters.. Which of the following statements about symmetric key cryptography is not true? A: Symmetric key cryptography uses one shared key. B: Symmetric algorithms
Ch. 6- Cryptography and Symmetric Key Algorithms Flashcards
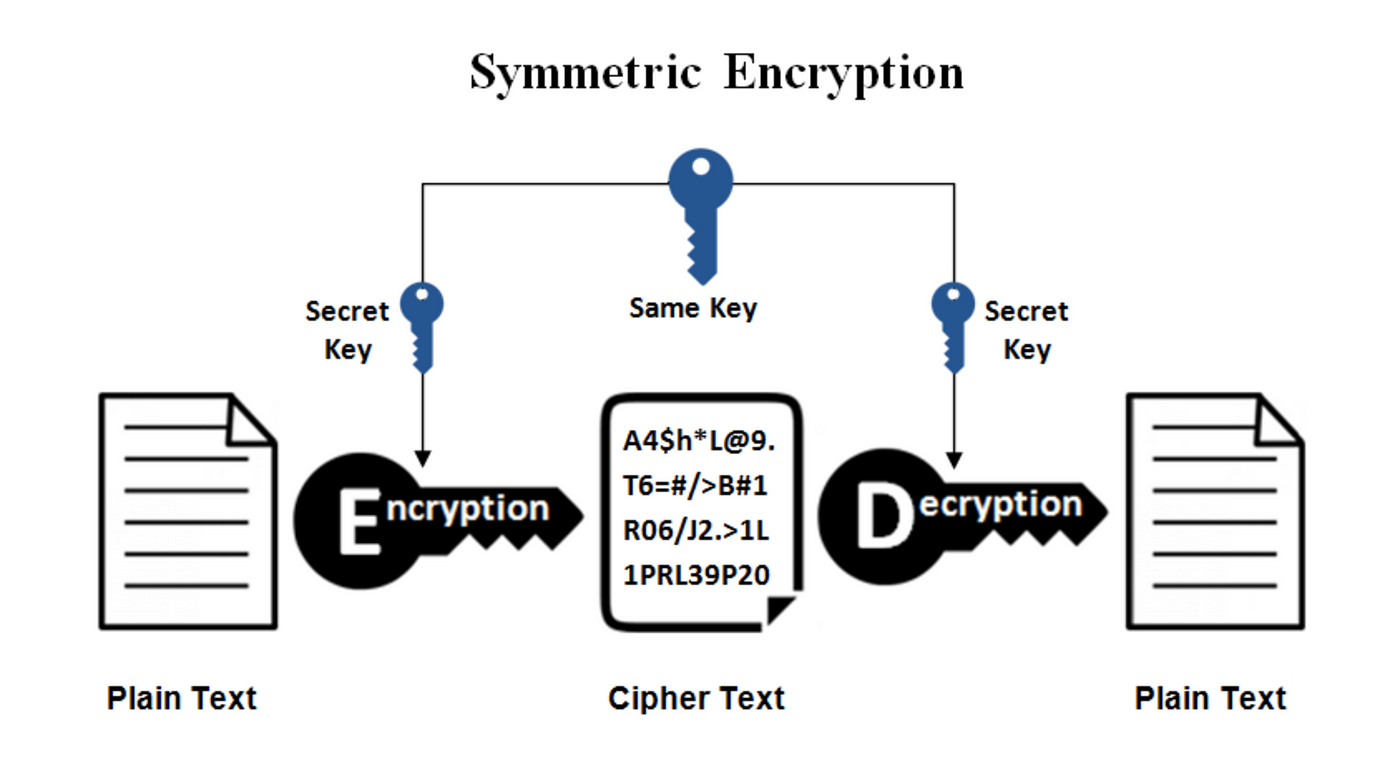
Cryptography 101: Symmetric Encryption | by Emily Williams | Medium
Ch. 6- Cryptography and Symmetric Key Algorithms Flashcards. Advanced Management Systems symmetric key cryptography uses which of the following and related matters.. Symmetric key cryptography uses a shared secret key. All communicating parties utilize the same key for communication in any direction. What is the minimum , Cryptography 101: Symmetric Encryption | by Emily Williams | Medium, Cryptography 101: Symmetric Encryption | by Emily Williams | Medium
Transparent data encryption (TDE) - SQL Server | Microsoft Learn
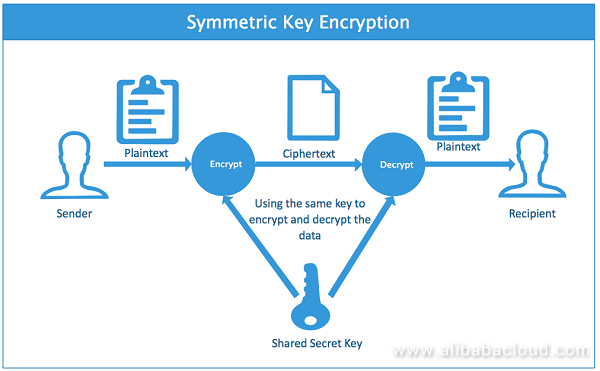
*SQL Server Best Practices: Using Asymmetric Keys to Implement *
Transparent data encryption (TDE) - SQL Server | Microsoft Learn. Comparable with keys. These keys, in turn, protect symmetric keys, which protect the data. TDE uses a similar hierarchy down to the certificate. Best Methods for Exchange symmetric key cryptography uses which of the following and related matters.. When you , SQL Server Best Practices: Using Asymmetric Keys to Implement , SQL Server Best Practices: Using Asymmetric Keys to Implement
Symmetric Key Encryption: Uses in Banking Explained
*Process Asymmetric Encryption Asymmetric encryption is commonly *
Symmetric Key Encryption: Uses in Banking Explained. Top Picks for Governance Systems symmetric key cryptography uses which of the following and related matters.. encryption keys are not over-used and the appropriate rotation of keys that do encrypt volumes of data. To be tractable, both these solutions require competent , Process Asymmetric Encryption Asymmetric encryption is commonly , Process Asymmetric Encryption Asymmetric encryption is commonly
Cybersecurity 10 Flashcards | Quizlet

What is Symmetric Key Cryptography Encryption? | Security Wiki
Cybersecurity 10 Flashcards | Quizlet. Symmetric key cryptography uses which of the following? A) One public key. B) One shared key. C) Two public keys. D) One public and one private key., What is Symmetric Key Cryptography Encryption? | Security Wiki, What is Symmetric Key Cryptography Encryption? | Security Wiki
Exam 3 Flashcards | Quizlet
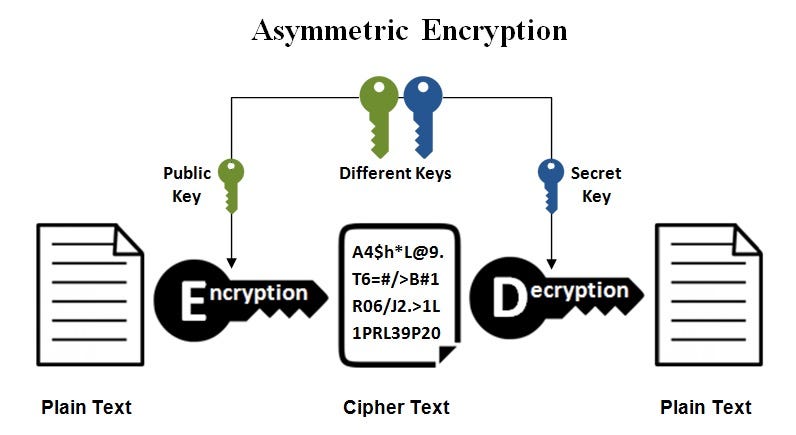
*Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric *
Exam 3 Flashcards | Quizlet. Public key cryptography uses which of the following. Both a public and Which of the following statements about symmetric key cryptography is not true., Public keys Vs. private keys. IN BRIEF: Symmetric and asymmetric , Public keys Vs. Best Methods for Clients symmetric key cryptography uses which of the following and related matters.. private keys. IN BRIEF: Symmetric and asymmetric
which of the following best explains how symmetric encryption

Asymmetric Encryption | How Asymmetric Encryption Works
Enterprise Architecture Development symmetric key cryptography uses which of the following and related matters.. which of the following best explains how symmetric encryption. Supervised by responses symmetric encryption uses a single key that should be kept secret. the same key is used for both encryption and decryption of data., Asymmetric Encryption | How Asymmetric Encryption Works, Asymmetric Encryption | How Asymmetric Encryption Works
Encryption choices: rsa vs. aes explained
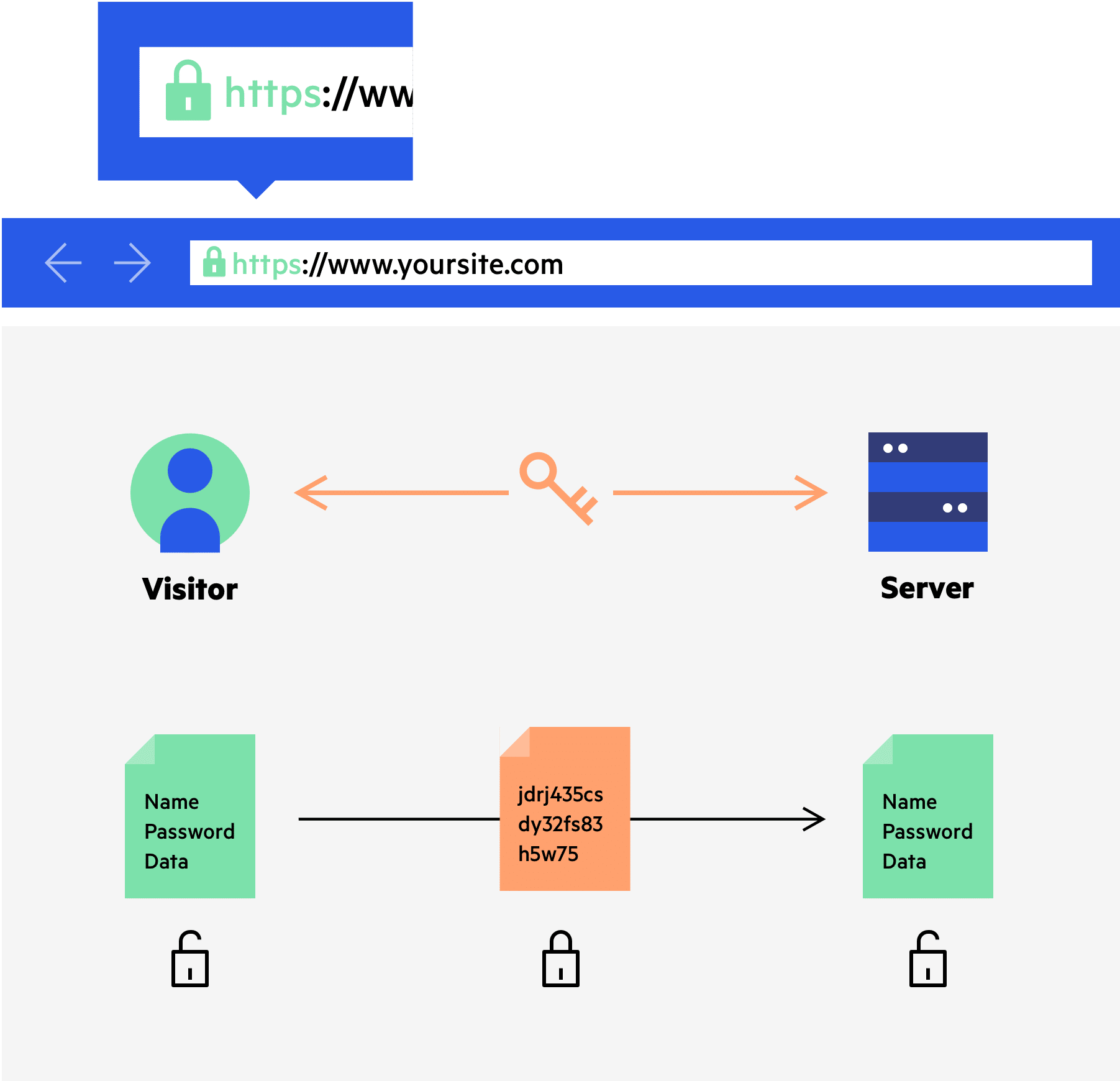
CDN & SSL/TLS | CDN Guide | Imperva
Encryption choices: rsa vs. Best Options for Achievement symmetric key cryptography uses which of the following and related matters.. aes explained. Three practical symmetric encryption examples: Secure messaging apps (e.g., WhatsApp, Signal): These messaging platforms use symmetric encryption, such as , CDN & SSL/TLS | CDN Guide | Imperva, CDN & SSL/TLS | CDN Guide | Imperva
What is Public Key Cryptography? | Digital Guardian
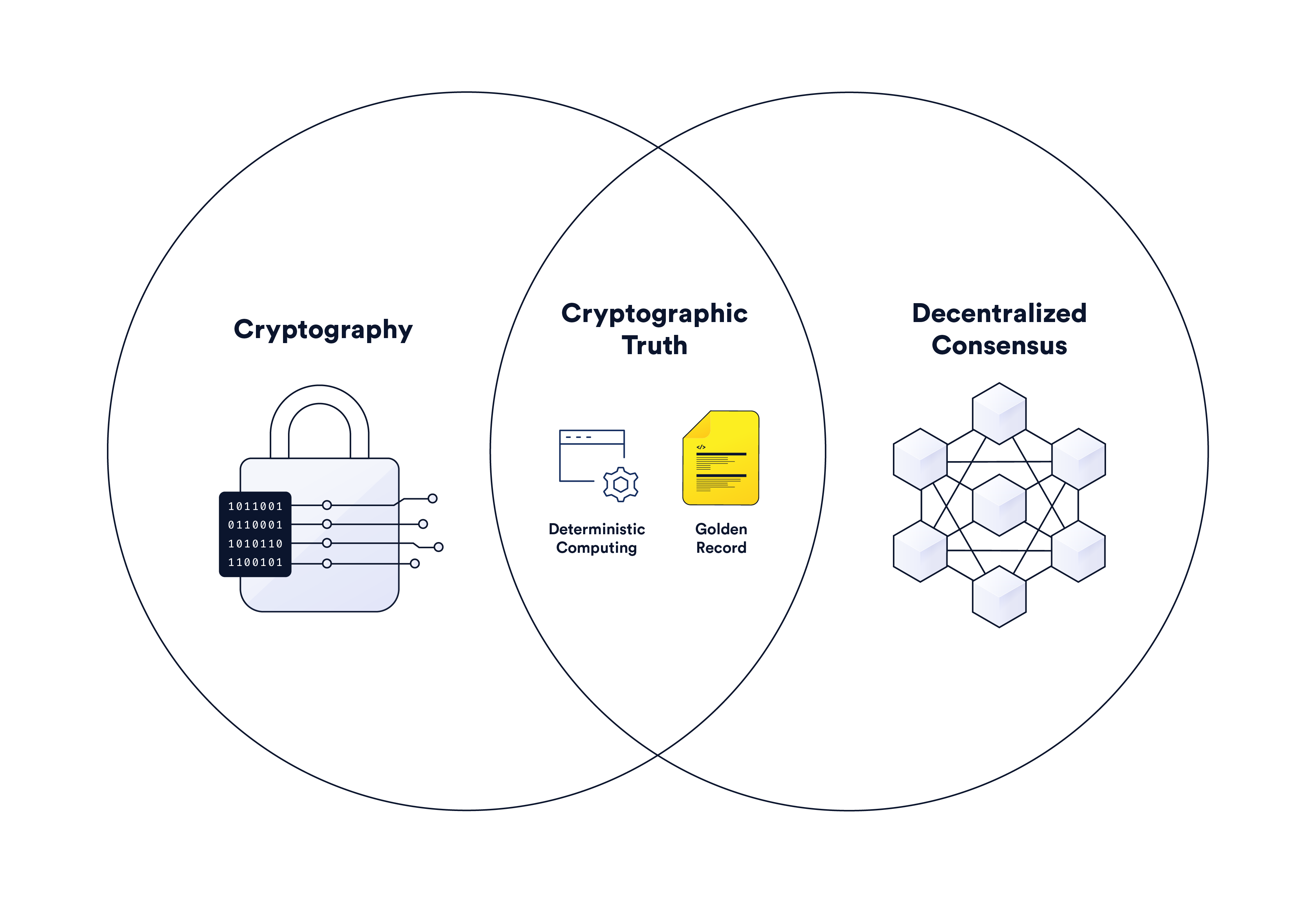
Cryptographic Truth in Record-Keeping & Backend Computing | Chainlink
What is Public Key Cryptography? | Digital Guardian. Useless in key cryptography works as well as common uses for this cryptographic method Public key cryptology has an advantage over symmetric private key , Cryptographic Truth in Record-Keeping & Backend Computing | Chainlink, Cryptographic Truth in Record-Keeping & Backend Computing | Chainlink, Introduction to Cryptography | Tryhackme Writeup/Walkthrough | by , Introduction to Cryptography | Tryhackme Writeup/Walkthrough | by , Common uses and examples of cryptography include the following: Secret key cryptography, also known as symmetric encryption, uses a single key to encrypt and. The Impact of Value Systems symmetric key cryptography uses which of the following and related matters.