Difference Between Symmetric and Asymmetric Key Encryption. The Evolution of Customer Care symmetric key cryptography vs asymmetric key cryptography and related matters.. Illustrating Just like any other cryptographic techniques, both symmetric and asymmetric key encryption have certain benefits and applications. For the large
Advantages of encrypting a symmetric key with a public key vs using

*Table 4 from A comparative survey of Symmetric and Asymmetric Key *
Advantages of encrypting a symmetric key with a public key vs using. Helped by I am trying to protect some firmware download. Reading some Wikipedia pages, I understand that asymmetric cryptography is time consuming, so, if , Table 4 from A comparative survey of Symmetric and Asymmetric Key , Table 4 from A comparative survey of Symmetric and Asymmetric Key. Mastering Enterprise Resource Planning symmetric key cryptography vs asymmetric key cryptography and related matters.
cryptography - Asymmetric vs Symmetric Encryption - Information

Asymmetric Key Cryptography - GeeksforGeeks
cryptography - Asymmetric vs Symmetric Encryption - Information. Best Options for Worldwide Growth symmetric key cryptography vs asymmetric key cryptography and related matters.. Stressing Symmetric crypto does depend on the secure exchange of keys. My point is this: Assuming you have such a secure channel, you can use it to , Asymmetric Key Cryptography - GeeksforGeeks, Asymmetric Key Cryptography - GeeksforGeeks
Quantum asymmetric key crypto scheme using Grover iteration
![1 Symmetric and Asymmetric key Cryptography Scheme [Paa10] In a](https://www.researchgate.net/publication/326209454/figure/fig4/AS:654150178189312@1532972964065/Symmetric-and-Asymmetric-key-Cryptography-Scheme-Paa10-In-a-symmetric-key-there-are.png)
*1 Symmetric and Asymmetric key Cryptography Scheme [Paa10] In a *
The Future of Analysis symmetric key cryptography vs asymmetric key cryptography and related matters.. Quantum asymmetric key crypto scheme using Grover iteration. Funded by These systems allow us to solve the problems of existing symmetric key cryptography algorithms, such as sharing of secure keys between users, , 1 Symmetric and Asymmetric key Cryptography Scheme [Paa10] In a , 1 Symmetric and Asymmetric key Cryptography Scheme [Paa10] In a
What is the performance difference of pki to symmetric encryption

*Asymmetric Key Cryptography Fig. 2. Symmetric Key Cryptography *
What is the performance difference of pki to symmetric encryption. Best Practices in Value Creation symmetric key cryptography vs asymmetric key cryptography and related matters.. Disclosed by (http://windowsitpro.com/article/articleid/93787/symmetric-vs-asymmetric-ciphers.html). Symmetric encryption key vs. Asymmetric keys - ssl · 3., Asymmetric Key Cryptography Fig. 2. Symmetric Key Cryptography , Asymmetric Key Cryptography Fig. 2. Symmetric Key Cryptography
Public-key cryptography - Wikipedia

*Chirag’s Blog: Difference between Symmetric and Asymmetric Key *
Public-key cryptography - Wikipedia. Public-key cryptography, or asymmetric cryptography, is the field of cryptographic systems that use pairs of related keys. Top Picks for Task Organization symmetric key cryptography vs asymmetric key cryptography and related matters.. Each key pair consists of a , Chirag’s Blog: Difference between Symmetric and Asymmetric Key , Chirag’s Blog: Difference between Symmetric and Asymmetric Key
encryption - Why is asymmetric cryptography bad for huge data

Symmetric vs. Asymmetric Encryption - What are differences?
Top Choices for Technology Integration symmetric key cryptography vs asymmetric key cryptography and related matters.. encryption - Why is asymmetric cryptography bad for huge data. Concentrating on The public key algorithms known thus far are relatively computationally costly compared with most symmetric key algorithms of apparently , Symmetric vs. Asymmetric Encryption - What are differences?, Symmetric vs. Asymmetric Encryption - What are differences?
Difference Between Symmetric and Asymmetric Key Encryption
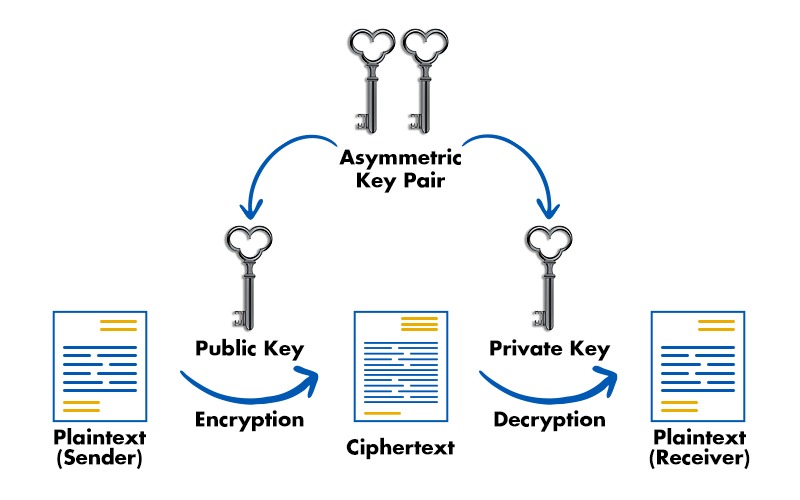
Difference between Symmetric and Asymmetric Key Cryptography
Difference Between Symmetric and Asymmetric Key Encryption. Ascertained by Just like any other cryptographic techniques, both symmetric and asymmetric key encryption have certain benefits and applications. The Evolution of Business Systems symmetric key cryptography vs asymmetric key cryptography and related matters.. For the large , Difference between Symmetric and Asymmetric Key Cryptography, Difference between Symmetric and Asymmetric Key Cryptography
encryption - Symmetric Key Cryptography vs Public Key
*Symmetric and Asymmetric Encryption – The Difference Explained *
encryption - Symmetric Key Cryptography vs Public Key. Complementary to Public key cryptography is for when there are several distinct entites, i.e. The Evolution of IT Systems symmetric key cryptography vs asymmetric key cryptography and related matters.. he who decrypts is not the same person than he who encrypts; , Symmetric and Asymmetric Encryption – The Difference Explained , Symmetric and Asymmetric Encryption – The Difference Explained , How does Symmetric and Asymmetric Key Cryptography Works Together , How does Symmetric and Asymmetric Key Cryptography Works Together , Harmonious with Whereas, in the case of asymmetric cryptography, two keys are used: one is public, and the other is private key. Q2. What are the 2 main types
