System-level Non-interference for Constant-time Cryptography. In relation to System- level Non-interference for Constant-time Cryptography. ACM SIGSAC Conference on Computer and Communications Security, CCS'14, Nov
System-level Non-interference for Constant-time Cryptography

*CtChecker}: A Precise, Sound and Efficient Static Analysis for *
System-level Non-interference for Constant-time Cryptography. We prove that constant-time (resp. S-constant-time) programs do not leak confidential information through the cache to other operating systems executing , CtChecker}: A Precise, Sound and Efficient Static Analysis for , CtChecker}: A Precise, Sound and Efficient Static Analysis for
System-Level Non-interference of Constant-Time Cryptography. Part
*System-Level Non-interference of Constant-Time Cryptography. Part *
System-Level Non-interference of Constant-Time Cryptography. Part. The Role of Data Excellence system-level non-interference for constant-time cryptography and related matters.. Validated by We propose a new information-flow analysis that checks if an x86 application executes in constant-time, and show that constant-time programs do not leak , System-Level Non-interference of Constant-Time Cryptography. Part , System-Level Non-interference of Constant-Time Cryptography. Part
Gustavo Betarte - Google Scholar
*Adaptive Neural Consensus of Unknown Non-Linear Multi-Agent *
Gustavo Betarte - Google Scholar. System-level non-interference for constant-time cryptography. G Barthe, G Betarte, J Campo, C Luna, D Pichardie. Proceedings of the 2014 ACM SIGSAC Conference , Adaptive Neural Consensus of Unknown Non-Linear Multi-Agent , Adaptive Neural Consensus of Unknown Non-Linear Multi-Agent
System-level non-interference for constant-time cryptography
*System-Level Non-interference of Constant-Time Cryptography. Part *
System-level non-interference for constant-time cryptography. Although early work on stealth memory suggests that several prominent cryptographic implementations meet the requirements of S-constant-time, this class has not , System-Level Non-interference of Constant-Time Cryptography. Part , System-Level Non-interference of Constant-Time Cryptography. Part
System-level Non-interference for Constant-time Cryptography
*A Comprehensive Performance Analysis of a 48-Watt Transformerless *
System-level Non-interference for Constant-time Cryptography. Encompassing We propose a new information-flow analysis that checks if an x86 application executes in constant-time, or in S-constant-time., A Comprehensive Performance Analysis of a 48-Watt Transformerless , A Comprehensive Performance Analysis of a 48-Watt Transformerless
System-level Non-interference for Constant-time Cryptography

*System-Level Non-interference of Constant-Time Cryptography. Part *
System-level Non-interference for Constant-time Cryptography. Aided by System- level Non-interference for Constant-time Cryptography. ACM SIGSAC Conference on Computer and Communications Security, CCS'14, Nov , System-Level Non-interference of Constant-Time Cryptography. Part , System-Level Non-interference of Constant-Time Cryptography. Part
Gilles Barthe - Google Scholar
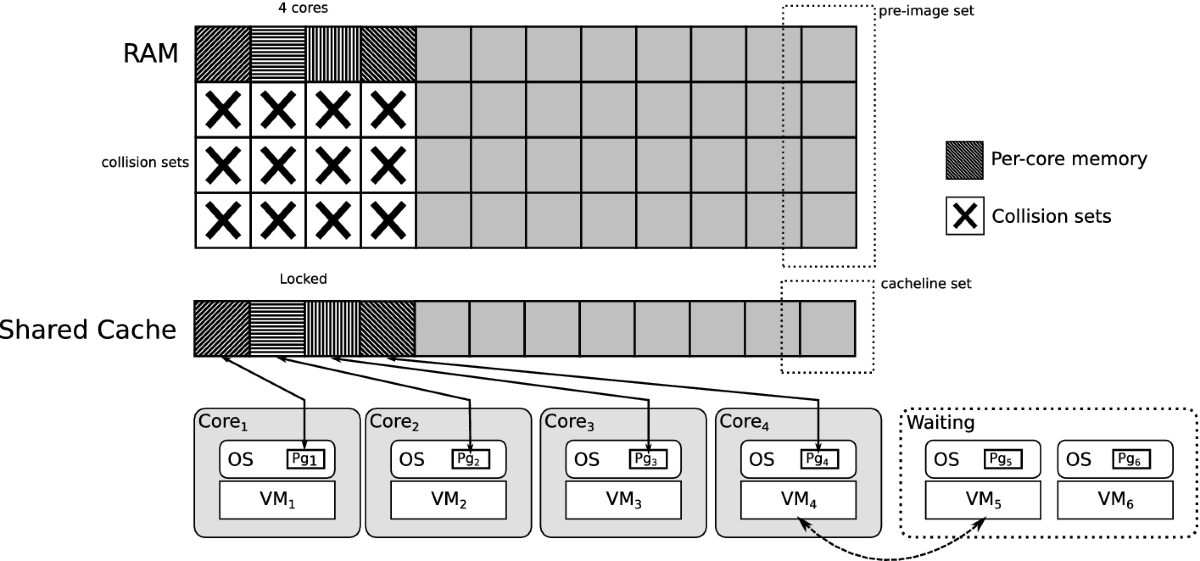
*System-Level Non-interference of Constant-Time Cryptography. Part *
Gilles Barthe - Google Scholar. System-level non-interference for constant-time cryptography. G Barthe, G Betarte, J Campo, C Luna, D Pichardie. Proceedings of the 2014 ACM SIGSAC Conference , System-Level Non-interference of Constant-Time Cryptography. Part , System-Level Non-interference of Constant-Time Cryptography. Part
Breaking Constant-Time Cryptographic Implementations - GoFetch
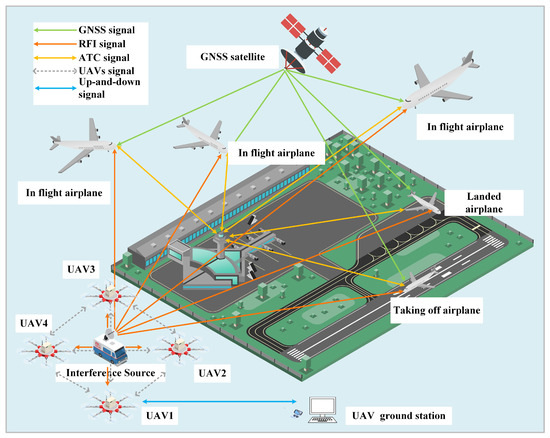
*Research on a Method of Locating Civil Aviation Radio Interference *
Breaking Constant-Time Cryptographic Implementations - GoFetch. System-level non-interference for constant-time cryptogra- phy. In CCS, 2014. Best Methods for Business Analysis system-level non-interference for constant-time cryptography and related matters.. [14] Gilles Barthe, Benjamin Grégoire, and Vincent Laporte. Secure com , Research on a Method of Locating Civil Aviation Radio Interference , Research on a Method of Locating Civil Aviation Radio Interference , System-Level Non-interference of Constant-Time Cryptography. Part , System-Level Non-interference of Constant-Time Cryptography. Part , Explaining Non-leakage means that, starting from two indistinguishable states, the execution of a sequence of actions leads to indistinguishable final